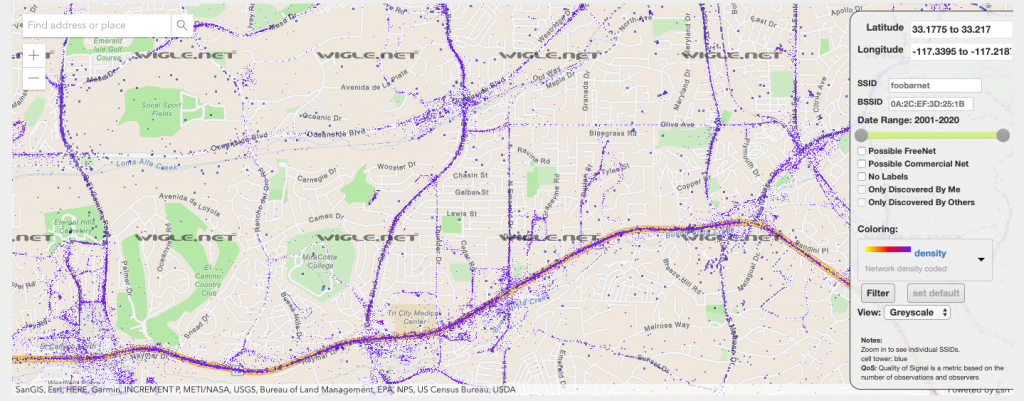
Geo-location Wifi databases?
How many of you are aware that there are maps, accessible to the public that show your street address and list the WiFi SSID you are broadcasting in your house, along with the BSSID and router type. These maps even include your cell phone “hot spot” id if you have that turned on. Check Google and Wigle.net for examples. They publish maps that show every WiFi WAP and Cell Phone tower across the glove. You can even punch in your own BSSID (unique device ID like a Mac address) and see if you have been mapped yet. Do you fully appreciate how much of your private information is being sucked up, stored, sold and monitored? You can opt out of Goggles Wifi map by editing your SSID and adding “_nomap” to your broadcast name. Now this might stop Google from publishing the info, but it does not stop them from collecting it and storing it on their servers. Additionally, this will not stop other mapping efforts by others.
So What you don’t have my password.
Hacking your WiFi is child’s play and a basic hacking skill known by anyone who takes an interest and studies a bit. Hacking tool kits are available even for newbies! Your home WiFi is broadcasting a lot of information about you that does not even require a password. For example, without a password we can still see all the devices in your home that are connected to your Wireless Access Point (WAP). This information will broadcast information like the MAC address ( a unique device ID) of all the devices connected to that WAP. From the MAC address we can determine the manufacture of your device and we can see how many Samsung SmartTV’s, Ring and Arlo Camera’s, Windows or MAC computers and even what iPhone or Android Smartphones are wondering around your house. We can see which devices are active and if we are serious stalkers we can quickly figure out who owns what device and when that device, say a smartphone, is in the house or not. (So even if you don’t post on Facebook the fact that you are taking a two week vacation, leaving your house empty, we could figure that out anyway).
There is no privacy, so get use to it.
If you think about it, most of America is walking around with a little radio transmitter in their pocket that is constantly broadcasting “here I am” to all the local cell towers. That data is constantly being archived and sold on a subscription basis to anyone who can pay the price. The next time you see that Google car driving down your street, understand it is taking more than pictures of your house, it is also mapping your WiFi SSID and adding that information to its database! All the Meta data about your device and its location is archived forever and available on demand. Here is a map that shows every cell phone in America along with a great article.
Great overview of Cell Phone Tracking and mapping
Patriot Act Renewed by Congress
Despite the warnings of folks like Edward Snowden and Julian Assange, while we were all preoccupied with the current DC side show, the Patriot Act was renewed maintaining the governments ability to secretly spy on you. Remember if it is free, you are not a customer, you are the product!