In his newly released ebook, Fonolo founder, Shai Berger, defines Abandoned Calls Rate as the Number of Abandoned Calls / Total Calls. Abandoned calls represent not only a lost revenue opportunity, but they cost you hard dollars. Shai does a masterful job at outlining these costs in a way that business folks can understand. Throughout my 35+ year career in telecommunications, I have witnessed the pain of Call Center management endlessly struggling to increase customer service levels and response times with limited available resources. One solution, hire more agents until there are no busy signals is never considered. Yet business managers never tire of adding more incoming telephone lines, queuing more and more customers to wait on hold for longer periods of time, resulting in lower customer service levels and higher abandonment rates!
Recently we heard of a company, HOLDYR, that actually makes a product that allows people to select what music they want to hear while on hold! As Shai points out in his book, if you think this is a joke, take a road trip with your browser open to onholdwith.com to see the rants of folks who have been on hold. Putting customers on hold will result in lost business and high frustration levels. You will also be tying up a phone line for the duration of that hold period. Couple that phone line to an incoming toll free number and the cost per minute of hold is even more dramatic. Only the IRS can leave folks on hold and care less about abandoned call rates, most competitive businesses prefer to take action.
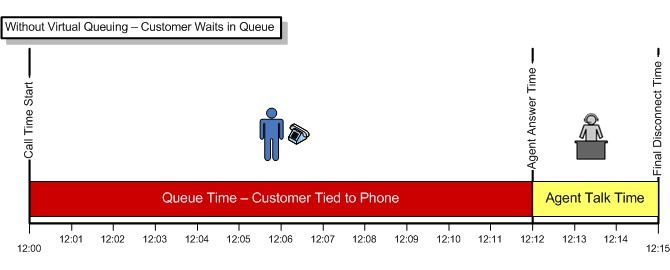
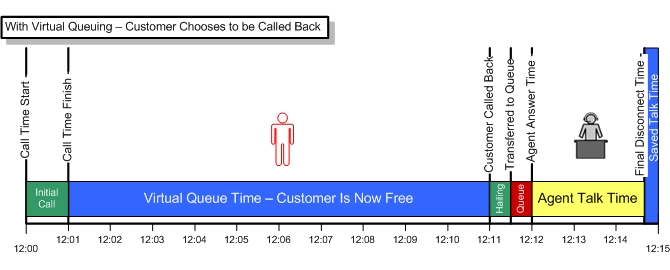
Call Backs offer reduced operating costs, smooth traffic demand, and fully employ customer service resources, so why not provide callers that option? After answering an incoming call and finding no agents are currently available, the caller is offered the option to “receive a call back without losing your place in queue”. If the customer elects this option, we can confirm their caller id or ask for the number we should call them back at. Fonolo offers a number of equipment agnostic “virtual queuing” solutions that can be added to an existing call center.
We can take this strategy to yet another level by providing call back options that do not even require a call to your customer service center at all! Web based call backs are one example, in which a client on your website provides a phone number and requests a call back. We are particularly fond of TEXT based solutions in which the customer sends a text message, and either receives a call back immediately, or receives a text with an estimated call back time. This text can prompt for an alternative call back number or time for call back. In both cases however, there is no need to queue callers or to have more telephone lines than you have customer service agents. (In fact, if you think about it, under the right conditions you might not need a call center at all!)
Send “TextMyECC” to 760-867-1000 for a sample interaction. We can even build these solutions around Smartphone apps which completely eliminate automated attendants, IVR and queuing, but allowing the customer to directly interact with the correct call center queue to schedule a “call back”!
[show_related ids=”1749, 1753 , 1699, 1598″]