The most often asked question we hear among ShoreTel system administrators is how best to achieve “fail over”, assure high availability and assure business continuity? There is no simple answer to this question nor is there any one “best practice”. It is going to depend on any number of interrelated issues including budget, facilities, availability and down time goals. With unlimited funding there are many more options then there are if we have a very limited budget. Is our deployment located in a single facility or scattered across multiple sites? Do we have an onsite data center or a “cloud” or collocation facility. Can we tolerate any down time at all or are we looking for hot fail over with no service interruption?
Redundancy by itself is not sufficient to guarantee high availability or continued uninterrupted business operations. Two power supplies are always better than one (especially if they are plugged into separate electrical sources) and RAID disk arrays are more reliable than a single spinning hard disk and iSCSI may even be a better. Many system administrators have explored commercial options like Double Take with its active/active fail over strategy.
At the end of the day, our view is that multiple hosts across multiple locations in a virtual or cloud based deployment are you best options. We think VMware and Amazon are unstoppable solutions providing high availability and business continuity assurance that maximizes budget, simplifies administration and with the lowest risk. Though we will have much more to say about Amazon Web Services, especially how it can best interface with VMware, we are going to demonstrate several configuration built on the vSphere ecosystem.
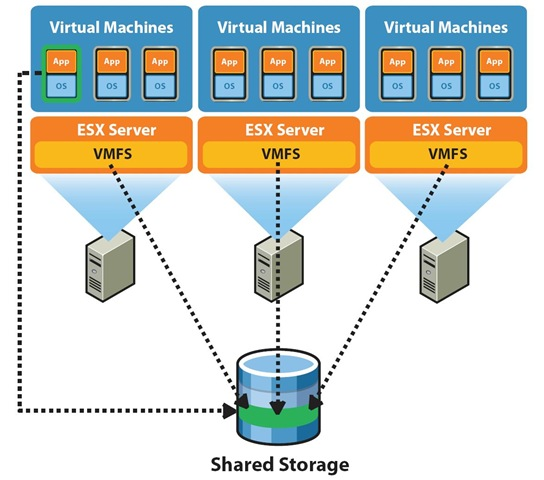
In our opinion your ShoreTel partner should have installed your deployment on VMware from the onset. A single VMware ESXi hypervisor host running your ShoreTel HQ Server and a ShoreTel Distributed Voice Mail server with the DVM installed at the same site and at the same level as the HQ server, will provide a very effective fail over solution at the lowest possible cost. VMware Essentials gets you ESXi and vCenter for $540, what is to think about? A single hardware host with two virtual Windows servers, a shared iSCSI data store and a copy of FreeSCO will best any effort to run redundant HQ servers! ShoreTel servers can fail up, so just put all of your HQ switches and Users on the DVM and if it fails, HQ will take over. If HQ fails, no real harm done.
Sounds like a lot of hardware complexity but we are going to demonstrate this on a lab system consisting of a single Windows Laptop! Through the miracle of VMware, Openfiler and FreeSCO we are going to create this entire solution and use it to prove out several different “fail over” strategies that can be used to develop “high availability” options for your ShoreTel deployment. Additionally if your are just learning VMware, this will be an excellent “play pen” and “sand box”and learning environment, well within the budget of any serious student of virtualization. If you can access a lap top the rest of the requirements can be obtained as open source “free ware” or evaluation software. So lets lose the excuses and get to work!
Building your “Sandbox”!
Our test environment will consist of 3 ESXi Hosts, an iSCSI data store, a CISCO compatible routers; two Windows servers; and two XP or better Windows PC’s. As this entire lab will be built out on a single device here is the “parts list”:
(a) Windows laptop – If you have several spare PC’s or servers that you can make use, of great but we can build out this entire test lab on a single laptop. The only requirement is that we need 16GB of RAM! as long as you can expand the memory to at least 16GB.
(b) Your first lesson in virtualization is to understand the difference between a type 1 and a type 2 hypervisor. VMware ESXi is a type 1 hypervisor and that means that it is installed on a bare metal host computer, typically an appropriately configured server. VMware Workstation is a type 2 hypervisor meaning it is installed on top of an operating system, like Windows, already installed on a bared metal hardware platform. In this case, we have a laptop running Windows 8 and we are going to install VMware Workstation on top of Windows. You can download an evaluation copy of VMware Workstation from http://www.vmware.com/products/workstation/workstation and when the 90 day evaluation is up, if you can find $249, it is our recommendation that no VoIP Engineer or Field technician should be without this a lap top running product.
(c) ESXi is a type 1 hypervisor and the really good news is it that it is still available absolutely free of charge. This will be the core of our test lab and we will build out three hosts, all running in VMware Workstation on our laptop, to support our ShoreTel deployment.
(d) Building out a ShoreTel HQ server under ESXi as a single server is what most folks do. If you are going for high availability, however, you need to consider the size of your data store. Even if you are only restoring a “snap shot”, the size of your data store may be the limitation that determines down time. Rather than store the application data on the Windows server used for your ShoreTel HQ erver, we recommend that you install an iSCSI data store on your LAN. In this way , if you have to restore the server, you will already have the data store available (this is where AWS S3 comes into play, so see our previous blog regarding backup strategies). You can download community edition of Openfiler the iSCSI data store we are going to deploy in this lab from http://www.openfiler.com/community/download as we will be configuring our deployment based on the availability of network area storage.
(e) One of the “must have” software tools in our Engineering laptop tool kit is a three interface router named FreeSCO! It is pronounced “Free CISCO”as a take off on our favorite company to hate. For those of you who ever wanted to deploy a fully functioning CISCO router from a USB drive, down load this now from www.freesco.org or download the ova we created which is available in the member portal of the DrVoIP web site.
(f) Lastly, you will need Windows Server software, either Windows 2008 or 2012. You can download an evaluation copy from Microsoft at http://msdn.microsoft.com/en-us/evalcenter/dn205302.aspx if you do not have a copy kicking around your lab.
(g) Lastly, ShoreTel has never asked for our opinion but they do not make evaluation software easily available to lab environments or to students who hope to be future ShoreTel VoIP engineers. ShoreTel software can only be legally obtained by purchasing a system or through a support agreement from either a ShoreTel partner or directly from ShoreTel TAC. If you are a partner or covered under a support agreement, you can down load all sofware from the ShoreTel site. The iPBX software will run license free for 45 days. Our lab is going to make use of the ShoreTel HQ server, the ShoreTel DVM Server and several virtual Shoregear voice gateways.
The DrVoIP video demonstrates how this lab is constructed and how the various components are installed and is part of the over all VMware training material available (or soon to be posted) on the DrVoIP website. This lab will enable you to not only become very comfortable with VMware in general, but help you explore the various options for providing high availability and business continuity to your ShoreTel deployment.