The economics of a “hosted” or “cloud” based data and voice service is generally based on moving costs between the hosted provider and your office. The most dramatic example is the cost of the Internet connection. There is an inverse relationship between bandwidth and the equipment location. The more voice and data services that are hosted or cloud based, the more bandwidth you will need to interconnect them to your office. Regardless of which model you go with, however, there are requirements for your “must have” premise equipment that will not change. For example, if your VoIP system is “hosted” in the “cloud”, or if it is located at your office premise, you will still need the very same list of computer network equipment. The equipment requirements for a Firewall, Router, Network Access and Control System, Power over Ethernet switches and phones will exist regardless of where the applications are hosted.
CISCO seems to continually push the marginal cost of adding phone service to that equipment list lower and lower each year. The CISCO Unified Communications Manager, including a fully featured Unity Connection voice messaging and VoIP Paging system with Jabber and presence can now be installed within your network router! If you have an office with less than 150 users and 300 devices, the marginal cost of adding CISCO Unified Collaboration features is basically the software license for the ISR-2900 series router that you will need to purchase anyway! Remember, with the hosted solution you still need to purchase phones and PoE switches to power those phones! Your local area network requires a router to interconnect it with the Internet to reach your service provider. Why not get a router that can act as your firewall, offer advanced intrusion detection and threat protection, and also provide a full range of Unified Communications features?

The BE6K is essentially the same Unified Communications Management and Collaboration solution that is provided in a family of CISCO Collaboration solutions built around the CUCM that ranges upwards of 30K end points! It provides advance phone system features, voice mail, and includes the Prime Collaboration Deployment tool to enable ongoing adds, moves and changes after your system is installed. Jabber enables you to stretch your office extension to anywhere you can carry your smartphone or Ipad! Optionally features include Teleconferencing and Unified Contact Center Express functionality. So what is there to think about?
For the technically oriented business manager, the Unified Communications functionality is running on a VMware ESXi engine installed inside the CISCO router. The normal CISCO router functions are augmented with a single slot blade server, the CISCO UCS E160D, 6 core, 2Ghz 16 GIG Ram processor that supports ESXi. Take a look at this screen shot!
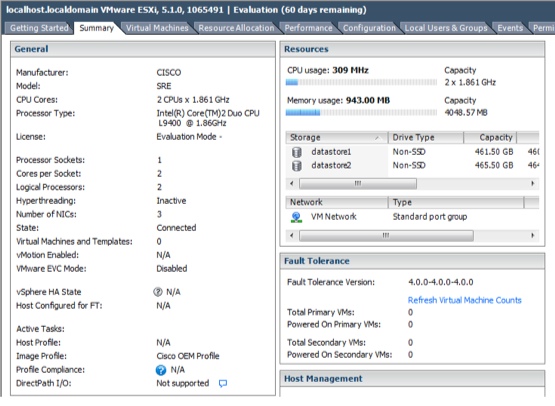
Think of the possibilities! Only a true geek could get this excited but really, VMware running inside a router!